Artificial Intelligence and its relationship with Big Data
Artificial Intelligence and its relationship with Big Data – For some people, artificial intelligence (AI) is something fiction writers use…
What is Data Driven Marketing and what is it for?
Data Driven Marketing – We could say that Data Driven Marketing is the strategy of strategies and we would not be falling…
Accelerated Mobile Pages
Accelerated mobile pages, also called AMP, is an open-source website framework that Google designs. This helps websites load quickly and…
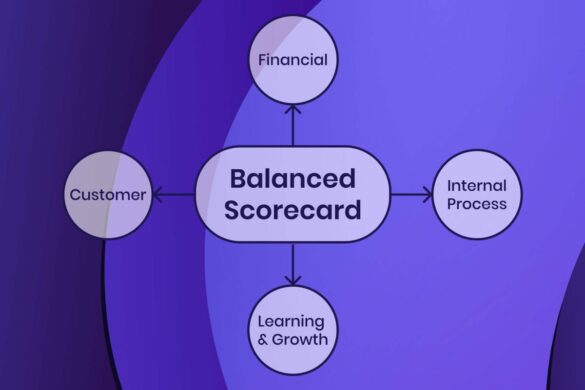
Balanced Scorecard
A balanced scorecard is a strategic management performance matrix to identify and improve internal business areas and resulting external outcomes….
Absolute Link
The absolute link, or the Absolute URL, is a web address containing the domain name, internet resources, and protocol. This…
Algorithm
The algorithm is a set of instructions that people follow in problem-solving operations or even mathematical calculations. It means it…
Call Management
Call management is the process or a system that is used by businesses to control incoming calls. It requires reliable…
Holistic Technology
Holistic technology is used to contribute to and support the overall community. It promotes a tremendous technological approach, including the…
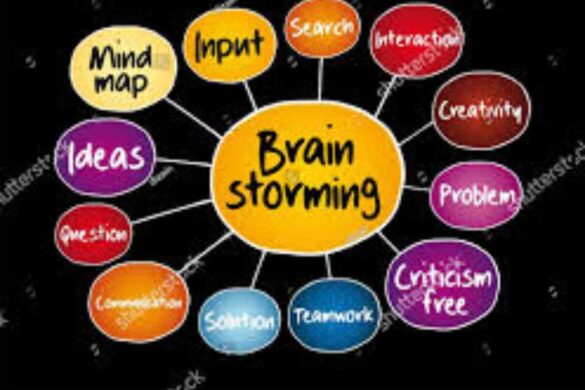
Brainstorming
Brainstorming is a creative thinking technique that will help develop new ideas and resolve any issues or errors. In many…
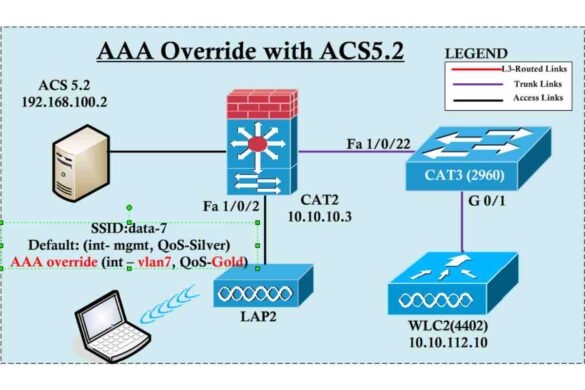
AAA Server
An AAA server It’s a program that handles a user request for access to any computer resources for an enterprise…